|
|
|
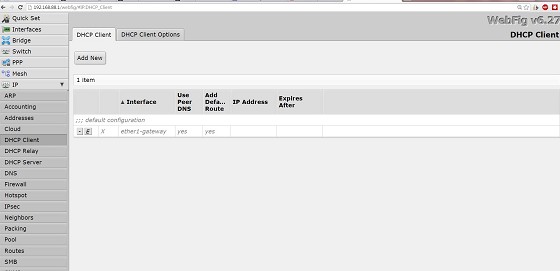
nitrotech: And just to tidy up you might want to remove the dhcp client from ether1 (if there's on there)
nitrotech: change 3rd rule to drop on pppoe interface -then click the nat tab and change the masquerade to pppoe interface then you should be sweet
mrzeke:nitrotech: And just to tidy up you might want to remove the dhcp client from ether1 (if there's on there)
this one ? So how is the DHCP working with out this? sorry im sure this is an idiot question...
mrzeke:nitrotech: change 3rd rule to drop on pppoe interface -then click the nat tab and change the masquerade to pppoe interface then you should be sweet
Again thanks for all your help today. Next step I am going to set up an access point that plugs into this Mikrotik. I am going to use a device than running DDwrt. Im not going to ask you for a step by step like you have provided me here but can you give me a couple of tips. Eg im assuming the Mikotik will do all the DHCP and the AP will just get tat information from the Mikrotik. any basic things you can advise me to do.
again thanks a lot. Have a great rest of your weekend !
zeke
MadEngineer: Lock it down before you get pwnd.
There are many firewall styles, best is to only allow new forwards (through traffic) generated by internal devices (amongst a dozen other required firewall filters). Google for mikrotik firewalling and copy one that includes that.
basic firewall operates in the manner of accept stuff you know about and absolutely drop everything else.
here's a question to make you think: how are devices on your network getting DNS? are you telling them all to get DNS from the Mikrotik? For that to work you'd need to enable remote dns requests ... are you only accepting dns from your internal devices?
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
MadEngineer: Here's a trimmed version of mine, basic run through if the comments are not enough:
drop all invalid. first to save invalid traffic hitting further rules
drop void addresses. this is a list of addresses that simply should not be generating traffic, including non-routed IP ranges that I'm not using locally.
accept local input. two things here, not just only blinding accepting local traffic but also only local traffic from known addresses.
accept traffic from PPP (VPN). if someone can correctly login over VPN, I trust them, so long as again they are known
accept established. if you can successfully connect, there's no point sending you through all the firewall rules again
accept VPN connections. self explanatory
accept limited pings. Mikrotik makes it easy to limit the number of pings
drop any other connections to the Mikrotik.
accept new forwards from local interfaces on local addresses.
allow related forwards. classically, ftp and other protocols.
accept Orcon. Esp VoIP
accept some port forwards. because of all the above, even if a port is opened in NAT through UPnP the traffic is blocked. these ports are for an internal service.
drop other forwards
NOT listed are a couple of effective fail to bans. Confucius say if you make a mistake x times, you're an idiot and can piss off for a while!
/ip firewall filter
add action=drop chain=input comment="Drop Invalid" connection-state=invalid
add action=drop chain=forward comment="Drop Invalid" connection-state=invalid
add action=drop chain=input comment="Drop Void" src-address-list=void
add chain=input comment="Accept Trusted" in-interface=Lan src-address-list=\
our-nets
add chain=input comment="Accept Trusted" in-interface=all-ppp \
src-address-list=our-nets
add chain=input comment="Accept Established" connection-state=established
add chain=input comment="IPSec, ISAKMP, L2TP" dst-port=4500,500,1701 \
protocol=udp
add chain=input comment="Accept limited ICMP" limit=50/5s,5 protocol=icmp
add action=drop chain=input comment="Drop Other Input"
add chain=forward comment="Accept local new forward" connection-state=new \
src-address-list=our-nets
add chain=forward comment="Accept related" connection-state=related
add chain=forward comment="Accept established" connection-state=established
add chain=forward comment="Accept Orcon (SIP)" src-address-list=orcon
add chain=forward comment="Accept port forward" dst-port=7940 protocol=tcp
add chain=forward comment="Accept port forward" dst-port=7940 protocol=udp
add action=drop chain=forward comment="Drop other forward" log-prefix=\
DropOtherFwd
|
|
|
