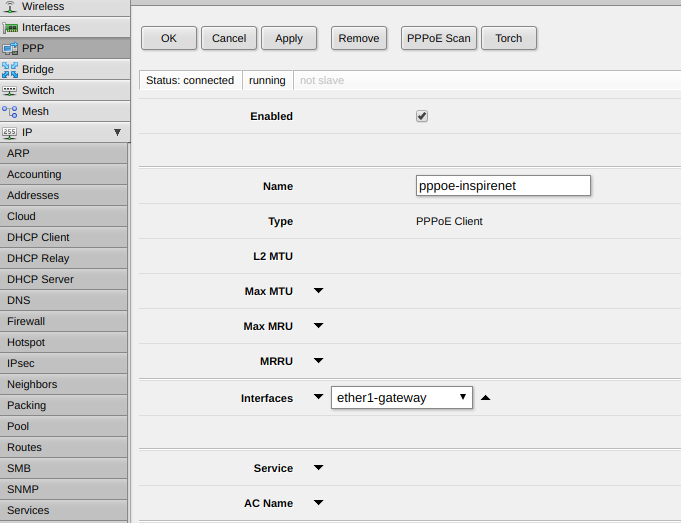
I'm trying to setup a new Mikrotik RB951G-2HnD router on Spark Fibre. I've followed the guide from @michaelmurfy here (http://www.geekzone.co.nz/forums.asp?forumid=66&topicid=161676) but I think the setup software is slightly newer now so some of the screenshots don't quite lineup and I'm not sure where I'm going wrong.
I've setup the quick setup screen like so:
Then I've added the VLAN info:
Then my interfaces screen doesn't look like the image in the guide, somehow I need to associate the VLAN with ether1-gateway, but there is no ether1-gateway, only ether1 in the VLAN screen???
Any help would be much appreciated - many thanks in advance!