For those who expose their Ubiquity router to the Internet, please run a Shields Up scan against your own device and post the results.
I'd like to know how yours compares to mine. Maybe a bit more tweaking via the CLI is required on my side.
For those who expose their Ubiquity router to the Internet, please run a Shields Up scan against your own device and post the results.
I'd like to know how yours compares to mine. Maybe a bit more tweaking via the CLI is required on my side.
Please keep this GZ community vibrant by contributing in a constructive & respectful manner.
|
|
Yeah you've got something a wee bit iffy with your firewall configuration:
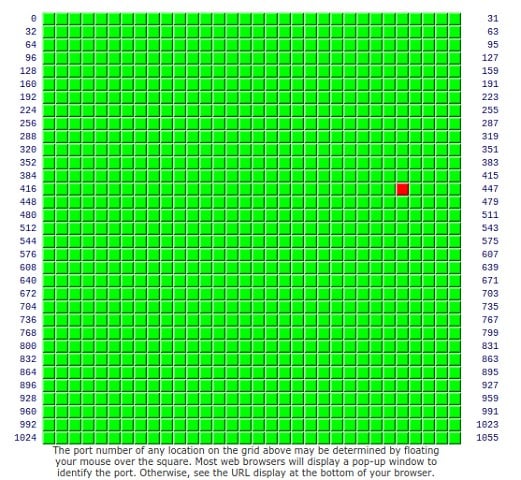
Did you follow the guide in my signature?
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
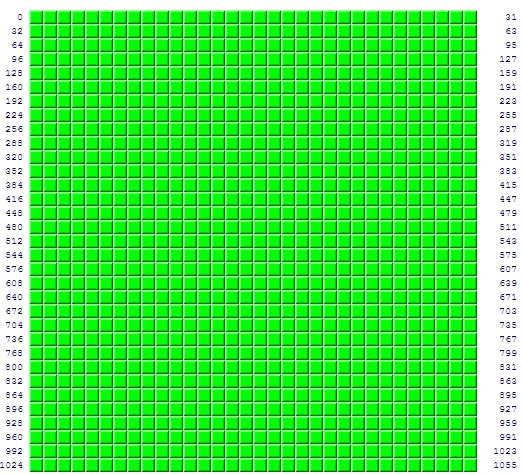
Mine looks fine, although I was following a guide from the best ![]()
PC: 5800X3D/32GB/RTX3070
Car: Toyota Celica GT-Four ST205
No issues with my ERL

All green and good - ERL and only using the default WAN rules from the intial setup.
"Your system has achieved a perfect "TruStealth" rating. Not a single packet — solicited or otherwise — was received from your system as a result of our security probing tests."
I don't know what you're worried about/testing for - packet filter firewall tests are relevant to the 1990s - not the present.
vulcannz:
I don't know what you're worried about/testing for - packet filter firewall tests are relevant to the 1990s - not the present.
Sorry but that is a broad sweeping statement. If more people used ShieldsUp we wouldn't have seen the rapid spread of WannaCrypt, or security cameras sitting on the public internet, etc etc.
vulcannz:I don't know what you're worried about/testing for - packet filter firewall tests are relevant to the 1990s - not the present.
jnimmo:
vulcannz:
I don't know what you're worried about/testing for - packet filter firewall tests are relevant to the 1990s - not the present.
Sorry but that is a broad sweeping statement. If more people used ShieldsUp we wouldn't have seen the rapid spread of WannaCrypt, or security cameras sitting on the public internet, etc etc.
Wannacrypt spread primarily by email phishing attacks. Users clicks an email and that links to a dropped, dropper brings in malware. The IPS portion of wannacrypt was based on an SMB attack that usually happened once a PC within a network was infected.
surfisup1000:vulcannz:
I don't know what you're worried about/testing for - packet filter firewall tests are relevant to the 1990s - not the present.
Can you explain why?
The way routers can shield the internal network hasnt really changed for several decades.
Do you mean ipv6 negates security as devices are exposed to the internet?
No, I mean most of attacks have transitioned from packet/port attacks into the data payload. Having a router that does packet filtering is all fine and dandy, but the bad guys have moved on from that type of attack (well except for DoS/DDoS's which is still going to kill a packet filter). Shieldsup is nice to check for open ports, but if you use it to give you any sense of network security you're greatly mistaken.
A typical attack will involve phishing, a dropper, then they bring in their malware. All this is usually happening over SSL encrypted sessions.
I don't think anyone was trying to use it as a measure of network security, but an indicator of insecurity. It is still important to know what ports are open, that you're not exposing management web interface or remote management ports.
jnimmo:
I don't think anyone was trying to use it as a measure of network security, but an indicator of insecurity. It is still important to know what ports are open, that you're not exposing management web interface or remote management ports.
Yeah that I understand, but still you did say "If more people used ShieldsUp we wouldn't have seen the rapid spread of WannaCrypt"
|
|
