Hi, i have been stuffing around with my working network to make administration a bit easier. How i would like it to work is have my ER Lite setup so it becomes the DHCP for all my vlans and then have the cambium access points centrally managed via the cloud admin tool. My problem at the moment is that everything on VLAN 1 is working fine but a seperate VLAN (30) does not appear to work as expected. The wifi client just gets stuck on trying to retrieve IP .
The E600 is set up as follows:
ACL:
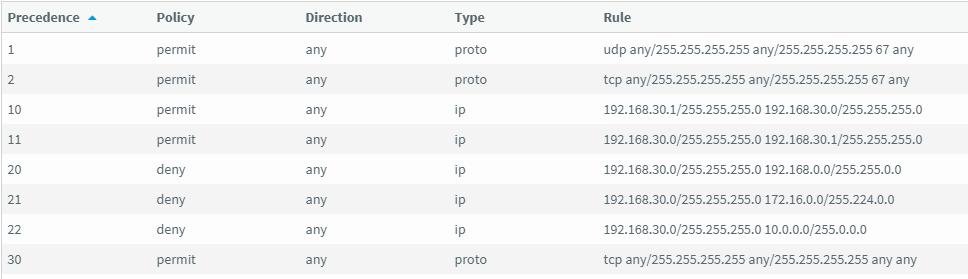
Trunk:
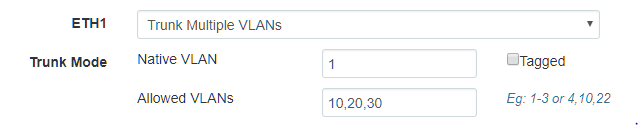
VLAN:
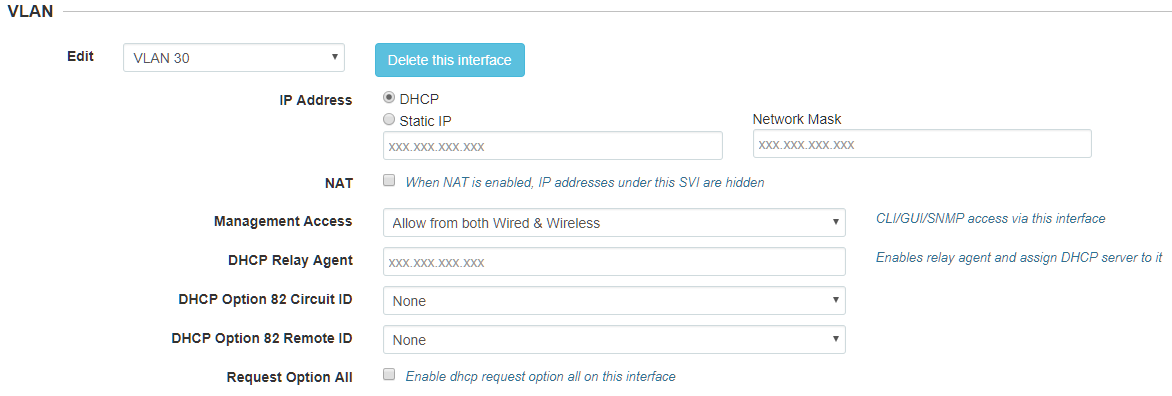
On my DLINK switch:
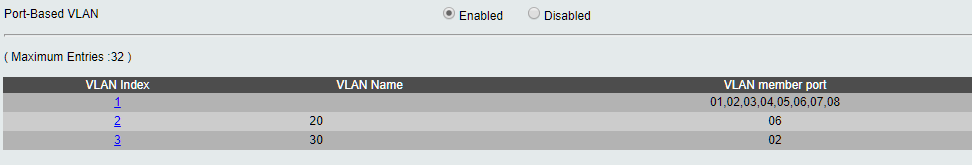
And finally, on the erlite:
firewall {
all-ping enable
broadcast-ping disable
group {
network-group IOT_VLAN_BLOCK_NETS {
description "Drop IoT traffic to other VLANs"
network 192.168.1.0/24
network 192.168.20.0/24
}
network-group LAN_NETWORKS {
description "RFC1918 LAN Networks"
network 192.168.0.0/16
network 172.16.0.0/12
network 10.0.0.0/8
}
network-group VIDEO_VLAN_BLOCK_NETS {
description "Drop Video Camera traffic to other VLANs"
network 192.168.20.0/24
}
}
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name IOT_WIFI_PROTECT_IN {
default-action accept
rule 10 {
action accept
description "Accept IoT WiFi Established/Related"
protocol all
state {
established enable
related enable
}
}
rule 30 {
action drop
description "Drop IOT_VLAN_BLOCK_NETS"
destination {
group {
network-group IOT_VLAN_BLOCK_NETS
}
}
protocol all
}
}
name IOT_WIFI_PROTECT_LOCAL {
default-action drop
rule 10 {
action accept
description "Accept DNS"
destination {
port 53
}
protocol udp
}
rule 20 {
action accept
description "Accept DHCP"
destination {
port 67
}
protocol udp
}
}
name WAN_IN {
default-action drop
description "WAN to internal"
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 30 {
action drop
description "Drop invalid state"
state {
invalid enable
}
}
}
name WAN_LOCAL {
default-action drop
description "WAN to router"
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action drop
description "Drop invalid state"
state {
invalid enable
}
}
}
options {
mss-clamp {
mss 1412
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
interfaces {
ethernet eth0 {
description "Internet (PPPoE)"
duplex auto
pppoe 0 {
default-route auto
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
}
mtu 1492
name-server auto
}
speed auto
}
ethernet eth1 {
address 192.168.1.1/24
description Local
duplex auto
speed auto
vif 30 {
address 192.168.30.1/24
description IoT
firewall {
in {
name IOT_WIFI_PROTECT_IN
}
local {
name IOT_WIFI_PROTECT_LOCAL
}
}
mtu 1500
}
}
ethernet eth2 {
address 192.168.2.1/24
description "Local 2"
disable
duplex auto
speed auto
}
loopback lo {
}
}
port-forward {
auto-firewall enable
hairpin-nat enable
lan-interface eth1
wan-interface eth0
}
service {
dhcp-server {
disabled false
hostfile-update disable
shared-network-name LAN1 {
authoritative enable
subnet 192.168.1.0/24 {
default-router 192.168.1.1
dns-server 192.168.1.1
domain-name xxxxxl
lease 86400
start 192.168.1.38 {
stop 192.168.1.243
}
}
}
shared-network-name VLAN30_IOT {
authoritative disable
subnet 192.168.30.0/24 {
default-router 192.168.30.1
dns-server 192.168.30.1
lease 86400
start 192.168.30.50 {
stop 192.168.30.100
}
}
}
static-arp disable
use-dnsmasq enable
}
dns {
forwarding {
cache-size 400
listen-on eth1
listen-on eth1.30
name-server 192.168.1.1
name-server 1.1.1.1
}
}
gui {
http-port 80
https-port 443
older-ciphers enable
}
nat {
rule 1 {
description "DNS Redirection"
destination {
port 53
}
inbound-interface eth1
inside-address {
address 192.168.1.1
port 53
}
log disable
protocol tcp_udp
source {
address 192.168.1.2-192.168.1.254
}
type destination
}
rule 5010 {
description "masquerade for WAN"
outbound-interface pppoe0
type masquerade
}
}
ssh {
port 22
protocol-version v2
}
unms {
disable
}
}
Please advise.
Image already added


