I am endeavouring to (re)configure my home network. Secondary purpose to learn something new about networking. Aiming to check I've got the principles right here before actually going to attempt to set it up in practice (on an Edgerouter Lite in my case).
If it matters, access to the internet is eth0.10, PPPOE.
Local network is all on eth1 via L3 switch and WAPs that support VLAN tagging.
Aim is to have four VLANS:
- Primary, for trusted devices (and things that don't work on other VLANS - Google Home, printers, TV)
- Kids, again trusted devices, but safe browsing via DNS filtering (PiHole and Safebrowsing.org)
- IOT, non-trusted but some access required
- Guest, non-trusted
The trusted VLANS should be able to access the non-trusted, but not vice versa. And the non-trusted VLANs should not be able to access each other.
Does this sound right for firewall rules (took me a long time to get my head around local, in and out so may have things wrong):
WAN_IN
- Allow established + related
- Allow forwarded ports (OpenVPN)
- Allow ping
- Drop everything else
WAN_LOCAL
- Allow establish + related
- Drop everything else
WAN_OUT
- Allow everything (this = no firewall rules?)
Primary + kids, in, out + local
- Allow everything (i.e. no rules)
IOT + GUEST_LOCAL (i.e. non-trusted VLANS to router)
- Allow established + related
- Allow DHCP
- Allow DNS
- Drop everything else
IOT + GUEST_OUT (i.e. trusted VLANS to non-trusted VLANS. I think???)
- Allow everything
IOT + GUEST_IN (i.e. non-trusted VLANS to trusted...?)
- Allow established + related
- Drop everything else
Does that sound right?
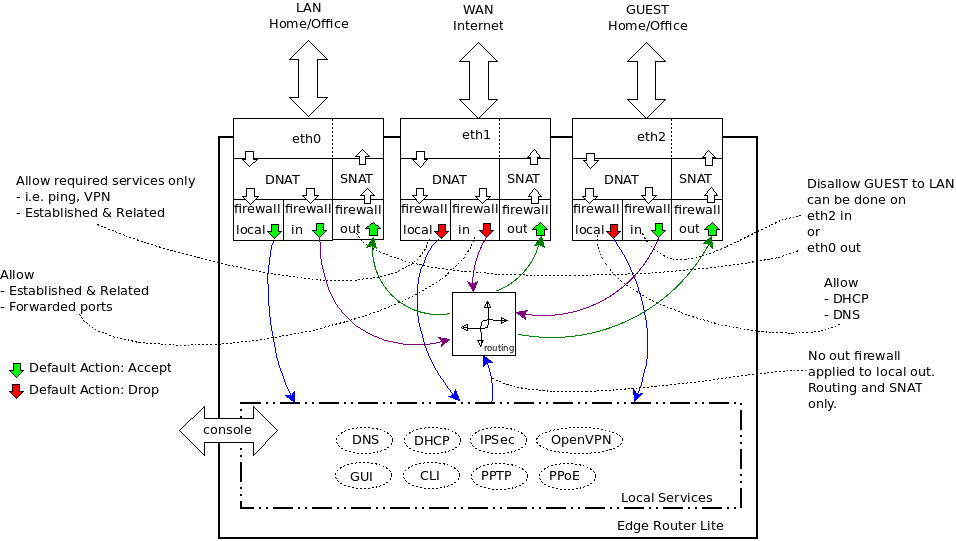
For anyone else looking, I found this diagram *super* helpful: