|
|
|
wipash: I'm seeing the same on Slingshot, with traffic to some specific CloudFlare IPs. Not 100% sure if these are Argo Tunnel IPs, or just IPs associated with CF's "proxy" feature.
I've been having the issue for weeks, but only started monitoring it yesterday. Even just from the last day worth of monitoring, there's an obvious pattern of packet loss related to time of day.
You would think Cloudflare Tunnel would be unaffected. But a few weeks checks out with what a friend of mine was seeing.
Here's mine on Quic. As you can see, no packet loss after over 100 pings and going direct out the IX:

The packet loss is what I don't understand here. I actually just helped out a friend tonight move away from Cloudflare Zero Trust Tunnels on Spark because they were seeing it drop all the time.
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
Here's my SmokePing, for anyone that wants to see how my 2degrees connection is holding up here:
https://smokeping.cvts.nz/smokeping
Ignore some of the gaps from today. I've got a freshly rebuilt server and reracked it, and SmokePing was offline for a few mins here and there - that's not representative of the connection. I also did some more tinkering to get IPv6 set up for my Docker bridge networks. I'll be tweaking my set of SmokePing tests over the coming days as well.
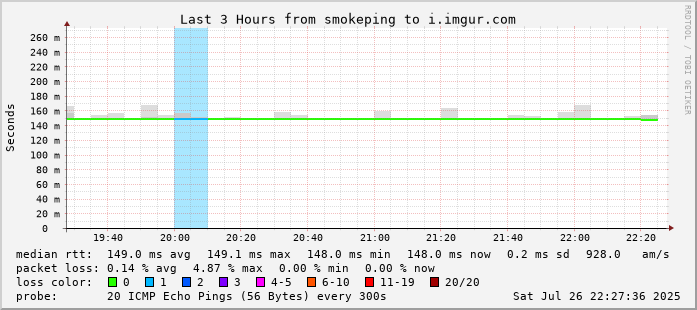
The imgur results are especially messy. Latency is variable, and the packet loss seems to be atrocious. I'm unsure if that's directly representative of the web performance, but it seems to be strongly correlated, at the very least.
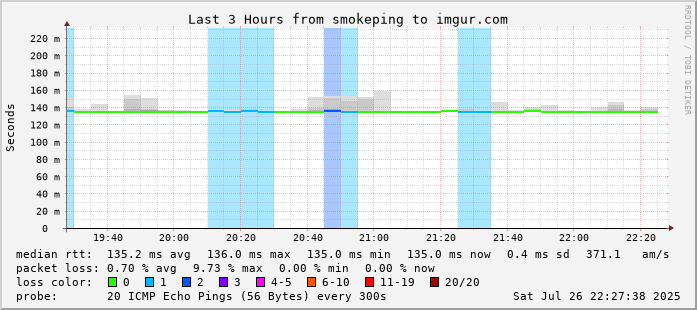
I switched to 2degrees DNS from Cloudflare DNS after seeing higher latency to Facebook and Akamai. This seems to have fixed up i.imgur.com (which is Fastly), but imgur.com is still bad and that site still struggles to load.
I wish i.imgur.com links were still direct links. I wouldn't notice any issues then. But sadly their direct image links redirect to their bloated website now. :(

I've been running some traceroutes, and noticing that things seem to go sour when they hit 101.98.5.93. I'm in Auckland, and that appears to be in Wellington, yet the host I'm connecting to is in the US.
Why is some traffic being routed through Wellington in the first place? And even more importantly, why does it seem to crap itself at that point?
ETA: It looks like it's going Auckland -> Wellington -> Auckland -> Sydney -> Perth -> San Francisco. What the heck?! That's an absurd route.
Tracing route to imgur.com [199.232.196.193]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms router.lan [192.168.88.1]
2 2 ms 2 ms 2 ms v1.akmod-bng1.tranzpeer.net [101.98.0.124]
3 4 ms 3 ms 2 ms default-rdns.vocus.co.nz [101.98.5.94]
4 * 14 ms 14 ms default-rdns.vocus.co.nz [101.98.5.93]
5 * * * Request timed out.
6 56 ms 42 ms * 124.150.165.62
7 40 ms * 41 ms 124.150.165.2
8 * * 37 ms 210.215.88.86
9 * 40 ms 39 ms 210.215.88.85
10 * 47 ms * 103-1-230-163.nexon.com.au [103.1.230.163]
11 * 64 ms 58 ms TenGigE0-0-0-6.bdr01-ipt-47bourke-syd.au.superloop.com [116.255.21.69]
12 * * * Request timed out.
13 * * 192 ms 103.200.13.168
14 167 ms * * 206.72.211.174.any2ix.coresite.com [206.72.211.174]
15 * 164 ms * 199.232.196.193
16 175 ms * 175 ms 199.232.196.193
Sony
sonyxperiageek: Has anyone gotten any further up the chain already with their ISPs out of curiosity?
I've tried. The problem is if it is the DIA filter (which I am now speculating it is) ISP's won't really say anything as they often can't but they can pass feedback onto the DIA.
There are good reasons why some things may be on the block (eg, Imgur, to a degree) but things like Cloudflare Tunnel make no sense. Hopefully they get this sorted but it's been going on for over 2 weeks now from what I can see and hasn't been resolved.
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
Link for public to appeal something if it is indeed on the DIA blocklist: https://dce.net.nz/appeal/index.html
My views are as unique as a unicorn riding a unicycle. They do not reflect the opinions of my employer, my cat, or the sentient coffee machine in the break room.
saf:
Link for public to appeal something if it is indeed on the DIA blocklist: https://dce.net.nz/appeal/index.html
I don't think anyone here in this thread has been met with the actual block page, it is more about degradation to all other internet traffic destined to the same IP address as a blocked site. Their own Code of Practice states:
3.1 The scope of the DCEFS is limited to preventing access to known websites that contain child sexual abuse material.
[..]
3.3 The DCEFS will not prevent access to any website or impair any Internet traffic that is not clearly within the scope as defined in paragraph 3.1.
There doesn't appear to be a clear process for reporting any impairment to any other Internet traffic by the filtering system.
It looks like at least from my end, anything going through cloudflare goes through this problematic route. In saying that, Akamai appears to not be impacted?
Though in saying that, My recent test I got a 24% packet loss. I personally think this has been going on for much longer than 2 weeks, it was only over the Christmas break I had a chance to start digging.
Just ran another test against a site I hosting in AU, using Cloudflare, I'm losing over 1/3 of all packets.
@Rudster yeah like the post at the top of this page by @wipash: https://www.geekzone.co.nz/forums.asp?forumid=81&topicid=318294&page_no=6#3333086
I’m seeing the exact same thing on other 2degrees connections.
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
Surprised it took this long to impact Cloudflare, if true. They must host - well, distribute (if we are going to nitpick) - some of the nastiest content on the internet, so it was going to be inevitable.
I can confirm that the Cloudflare Relay IP mentioned above is also impacted by the filter:
traceroute to 104.21.16.1 (104.21.16.1), 20 hops max, 46 byte packets
1 *
2 101.98.0.66 17.149 ms
3 101.98.5.93 28.466 ms
4 *
5 124.150.165.62 56.482 ms
6 *
7 *
8 *
9 *
10 *
11 *
12 *
13 *
14 *
15 *
16 *
17 *
18 *
19 *
20 *
I've raised INC0566456 with 2degrees. Let's see if this generates any meaningful response.
|
|
|
