|
|
|
Dynamic: Bugger.
To that MSP, feel free to reach out to us for extra manpower at no cost. It could potentially have been any of us.
Yup offer is open here as well.
networkn:Dynamic: Bugger.
To that MSP, feel free to reach out to us for extra manpower at no cost. It could potentially have been any of us.Yup offer is open here as well.
This kind of thing has been on my minds every since the solar winds hack. The minute you have software that gets updates without your interaction from an external vendor you are at risk of that vendors systems being compromised.
There was a massive similar hack some time back in the Ukraine with an accounting system where hackers got into the update servers at the software vendor and pushed encryption malware out to their customers.
Its a scary world with so much money available to hackers
I long for the old days where a virus did something innoculous like posting a message "You PC is now stoned. Legalise marijuana"
Matt Beechey Mobius Network Solutions
Thanks @sampler, @networkn, @Dynamic and any other person/organisation (here on Geekzone or not) helping out.
Please support Geekzone by subscribing, or using one of our referral links: Samsung | AliExpress | Wise | Sharesies | Hatch | GoodSync | Backblaze backup
If anyone needs boots on the ground in Wellington please let me know
Any views expressed on these forums are my own and don't necessarily reflect those of my employer.
Feel terrible for the MSP. I can't imagine what this would be like.
I'm also happy to take some volunteer days from work and help out where I can (Kapiti / Wellington region) if anyone here is affected free of charge. I can also get others in my workplace to take volunteer days to assist if additional manpower is required.
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
BleepingComputer - REvil ransomware hits 1,000+ companies in MSP supply-chain attack
Ransomware gang demands a $5 million ransom
A sample of the REvil ransomware used in one of these attacks has been shared with BleepingComputer.
However, it is unknown if this is the sample used for every victim or if each MSP received its own ransom demand.
The ransomware gang is demanding a $5,000,000 ransom to receive a decryptor from one of the samples.
a screen capture of the ransom demand :
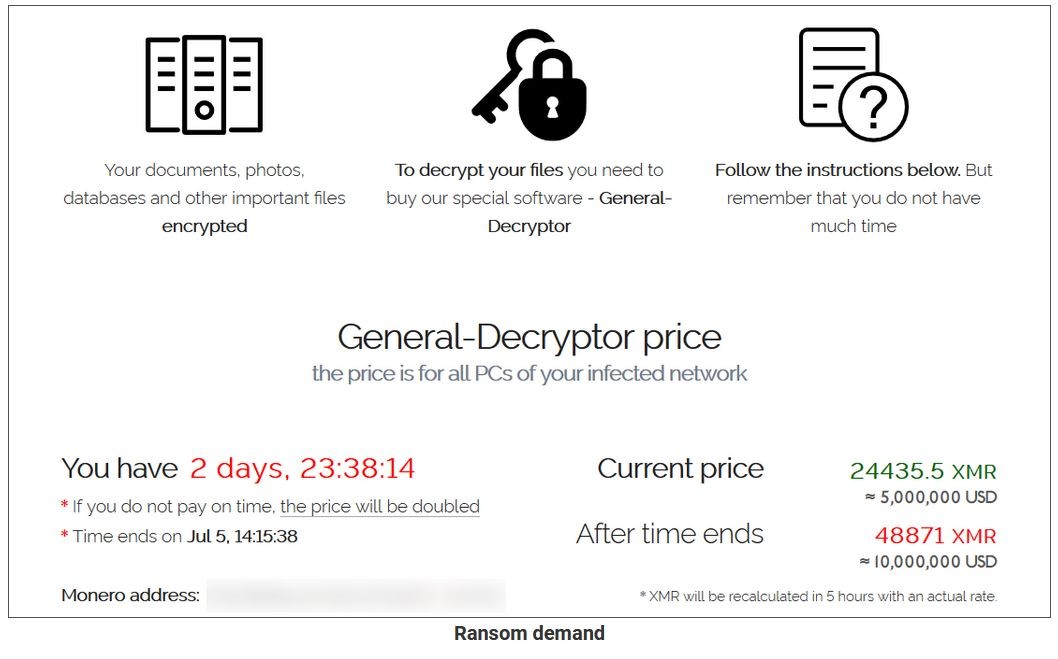
I hope that I never get to see one of these. 😶
Sideface
Happy to help out as well, Based in Auckland but have staff in Christchurch and spare gear
Also an update from Kaseya
https://www.kaseya.com/potential-attack-on-kaseya-vsa/
Updates Regarding VSA Security Incident
July 4, 2021 - 5:30 PM EDT
Next Update will be published July 4th in the very late evening EDT. Checking this link is the fastest way to ensure that you have the latest information from Kaseya.
Kaseya’s VSA product has unfortunately been the victim of a sophisticated cyberattack. Due to our teams’ fast response, we believe that this has been localized to a very small number of on-premises customers only.
Our security, support R&D, communications, and customer teams continue to work around the clock in all geographies to resolve the issue and restore our customers to service.
This update provides further detail on the July 4, 2021 10:00AM EDT and earlier updates.
Our efforts have shifted from root cause analysis and mitigating the vulnerability to beginning the execution of our service recovery plan. This plan will consist of the following stages:
Continued Advisory
michaelmurfy:
Feel terrible for the MSP. I can't imagine what this would be like.
While I would expect an even smaller number in nz, I could be interesting to know if any of those MSP's (and their customers) now affected had already jumped ship from solar winds with their breach that when public earlier this year. Sometimes it can be more prudent to stay with a platform after such events as they have usually completed more in depth audits and found/fixed all sorts of things.
Having said that, off the top if my head im not aware of any MSP tool set vendors who have provided confirmation of code or system auditing publicly. Maybe this point should be stressed to vendors ?
I'd not spotted that @billgates. Email sent.
“Don't believe anything you read on the net. Except this. Well, including this, I suppose.” Douglas Adams
Referral links to services I use, really like, and may be rewarded if you sign up:
PocketSmith for budgeting and personal finance management. A great Kiwi company.
On it.
Damn, they are good! Huntress responded already advising their partner has enough help for now. (Others, perhaps email your offer anyway just in case something comes up.)
“Don't believe anything you read on the net. Except this. Well, including this, I suppose.” Douglas Adams
Referral links to services I use, really like, and may be rewarded if you sign up:
PocketSmith for budgeting and personal finance management. A great Kiwi company.
Huntress are one of the good guys. The CEO is a total badass as well.
Thanks @billgates - have fired them an email. We also did attempt to get in contact with the MSP via Cert offering manpower. It is great to see everyone getting together and offering assistance despite this MSP being a competitor in many cases.
Edit: Just had a reply back saying they're blown away by the amount of responses they've gotten and said they don't have any unfulfilled requests.
Michael Murphy | https://murfy.nz
Referral Links: Quic Broadband (use R122101E7CV7Q for free setup)
Are you happy with what you get from Geekzone? Please consider supporting us by subscribing.
Opinions are my own and not the views of my employer.
|
|
|
