|
|
|
If this is true then it's pretty messed up and poor form on Kaseya's part
Beccara:
If this is true then it's pretty messed up and poor form on Kaseya's part
Good write up here (That you might have read)
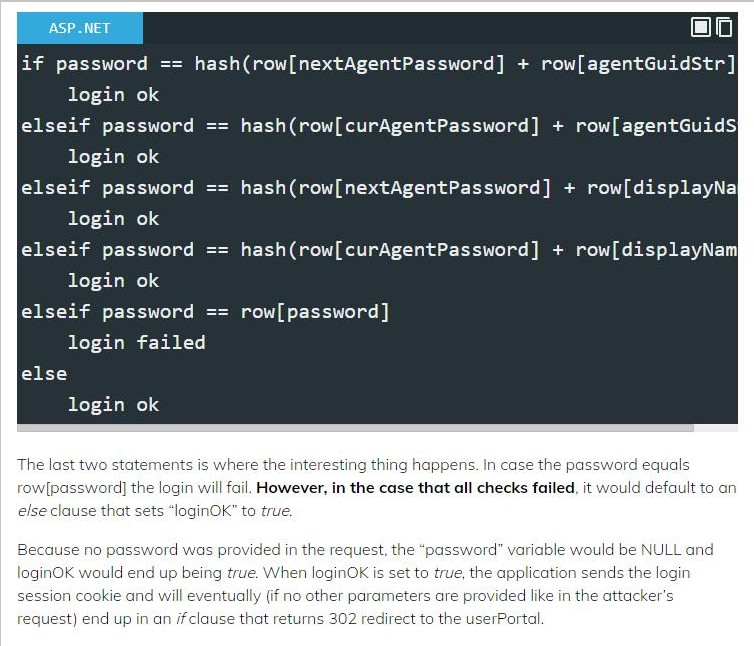
https://blog.truesec.com/2021/07/06/kaseya-vsa-zero-day-exploit/
That code example looks like a case of some seriously lazy programming with noone looking over the code - I know its pseudocode as an example but its supposed to be indicative of the real code. Basically "I can't think of a way we'd come out the bottom of this If/Else block of code so I'll just slap a Else login ok at the bottom" where if should have been an Else login failed."
Its scary how many exploits recently have been the result of someone finding a GAPING hole that should have been found in a code review.
The whole Microsoft Exchange flaw revolved in part around the fact that there was a hard coded with the same HMAC key on all installs where it should have had a randomly generated key for each install.
I know hackers are so well monetised now which is why they are getting some much more effective but it still seems often the flaws found by external people should have been easily found by people with the actual source code.
Its a scary world.
Matt Beechey Mobius Network Solutions
Considering the maximum amount of claim under the Kaseya MSP agreement is 2 months of costs, and whilst I haven't seen one recently, acts of terror or war used to be excluded, it doesn't seem likely they will be punished severely for their woefully poor coding practices. Some MSP's may move away, and secretly they may contribute to MSP's costs, most MSP's probably hold the view that moving RMM provider isn't likely going to afford them significantly better security and that it could have been any single one of the top 5 RMM providers that got hit instead.
To some degree the age and size of the codebase will have some bearing on how secure a product might be. That Makes Connectwise and Kaseya the two potentially worst to be with, especially since they are the two worst for saying but not doing the right things in my experience.
To Kaseya's credit, however, they have offered all Kaseya customers free WAF, which is a positive step, and likely, their management and lawyers are insisting on code reviews for all authentication and privilege escalation.
The problem is, and continues to be, that it takes far too long for issues like this to be plugged. They were advised in April. In my business, if something like this is identified, it's a 'everyone stop what you are doing, and don't do anything else until it's fixed' type scenario.
The partner in NZ who was hit, I wonder if the Fair Trading Act will trump the agreement they signed, giving them some level of recourse legally? Of course the costs of this are likely huge and massively time consuming.
Looks like a decryption tool has been created. :)
Opinions are my own and not the views of my employer.
CYaBro:
Looks like a decryption tool has been created. :)
The Kaseya Ransomware Nightmare Is Almost Over | WIRED
Created or bought?
It's going to be too late for the Victims of this attack surely? You'd either already have paid, restored from backup, or decided to do something else for a living if your systems had been down as long as this?
I mean, don't get me wrong, good work on getting it.
Cynic in me says a middle man "created" the tool for the price of the uber-ransom + 10%.
Beccara:
Cynic in me says a middle man "created" the tool for the price of the uber-ransom + 10%.
Why +10%? Why would anyone pay more when the original offer would have given them the same thing for 10% less?
Cover/Spin, "see we totally didn't pay the bad guys!" very few large companies pay the ransom but there seems to be a trend of external parties coming in to help them decrypt. Sometime they are legit and the bad guys used the same key on everything/everyone but there's always a few ones where eyebrows have been raised about suddenly being able to decrypt something that was well built
networkn:
Beccara:
Cynic in me says a middle man "created" the tool for the price of the uber-ransom + 10%.
Why +10%? Why would anyone pay more when the original offer would have given them the same thing for 10% less?
Not sure if possible but it might be they had some insurance that might have chipped in even with all of the "War on hacking" exclusions etc.
Its all very well to say "Never pay extortion money" but if someone has a gun to a family members head and paying is likely to see them safe people will do it. We are all selfish and do whats best for us not best for society as a whole.
Matt Beechey Mobius Network Solutions
It's certainly a little fishy that the tool is behind an NDA and hasn't just been sent to every client by default
|
|
|
