There is an item on RNZ about the Travelex ransomware attack. I have never experienced one, or any other attack, but I am wondering if anyone has? What happened?
|
|
|
They had an unsecured VPN, it encrypts server disk and asks for an unlock code that you only get by paying usually via bitcoin.
The company I was at back in 2014~ got hit by a variant of cryptolocker which took one of our site offline for a couple of days caused by a user opening a email attachment. Luckily we had pretty good monitoring in place so we picked up on it early and were able to lock down the WAN to prevent it spreading to other sites / our data centers.
We ended up restoring the server from backup (daily off site backups meant at most we lost a couple of days of data) and re-imaging the PCs.
<#
.DISCLAIMER
Anything I post is my own and not the views of my past/present/future employer.
#>
sqishy:
They had an unsecured VPN, it encrypts server disk and asks for an unlock code that you only get by paying usually via bitcoin.
This is simplistic and wrong. Yes, an unpatched VPN seems to have been the vector. No the "unsecured VPN" is not responsible for encrypting the server disk, but rather someone had access by exploiting a vulnerability in the unpatched VPN and having the cryptolocker installed.
Interesting topic, as just this week I was communicating to someone who had their systems affected and managed to decrypt everything without paying the ransom - basically explained to the bad actor that they were not a business and couldn't afford the amount of money asked. I have screenshots and videos, will post on another thread later.
Please support Geekzone by subscribing, or using one of our referral links: Samsung | AliExpress | Wise | Sharesies | Hatch | GoodSync | Backblaze backup
Prior to a few weeks/months ago, so long as you had good backups, there was really no need to consider paying a ransom. Since Ransomware has become such big business and IT has caught up and is moving toward doing a better job of protecting against it, the criminals have decided that to get around the "if you have a backup they won't pay" by now threatening to release a copy of the data they took when they encrypted. So even if you have a backup, there are some people who will likely need to pay to avoid the release of what could quite possibly be sensitive or privileged information.
IT Service Providers are now a big target. There have been some HUGE hits deployed by compromising the MSP/IT Provider, and using the IT providers links to their customers to encrypt the customers.
It's a scary world out there now.
work got hit last year (corporate hq overseas). expensive, as it was pegged at roughly $1M/day for 3 weeks.
recovered by restoring backups, but the time it took to ensure that all clients all over the world is "secure" before granting network access was a pain in the but.
it is real. it has a quantifiable monetary value.
CBS 60 minutes in Aug 2019 did a great report on just this topic which I saw when it aired (FTA) on Prime:
How cybercriminals hold data hostage... and why the best solution is often paying a ransom
Then a side report they did: Ransomware: Prevent your computer from being infected
The bit I found interesting is that one victim, Atlanta city, refused to pay the demanded $50,000. Instead, the city spent $20 million to recover on its own.
As I have always told all my friends and relatives - backup - backup - backup but the clever crooks can get around that as well by putting in time delay coding so your backups are infected as well.
Whilst the difficult we can do immediately, the impossible takes a bit longer. However, miracles you will have to wait for.
FineWine:this is why you must employ a proper backup rotation scheme. Any failure to backup properly means you’re simply not running a backup.CBS 60 minutes in Aug 2019 did a great report on just this topic which I saw when it aired (FTA) on Prime:
How cybercriminals hold data hostage... and why the best solution is often paying a ransom
Then a side report they did: Ransomware: Prevent your computer from being infected
The bit I found interesting is that one victim, Atlanta city, refused to pay the demanded $50,000. Instead, the city spent $20 million to recover on its own.
As I have always told all my friends and relatives - backup - backup - backup but the clever crooks can get around that as well by putting in time delay coding so your backups are infected as well.
I've seen a two fake ransomware infections.
The people I help can't tell the difference and I only just stopped one paying the money. There is some sort of user interface locking to make it hard for them to check.
Yes, I must admit that I made a mischievous blog post recommending that people take advantage of this ignorance.
I recommended a quick Google image search for WannaCry wallpaper, which they should download & set as desktop wallpaper. Next, right-click, hide icons.
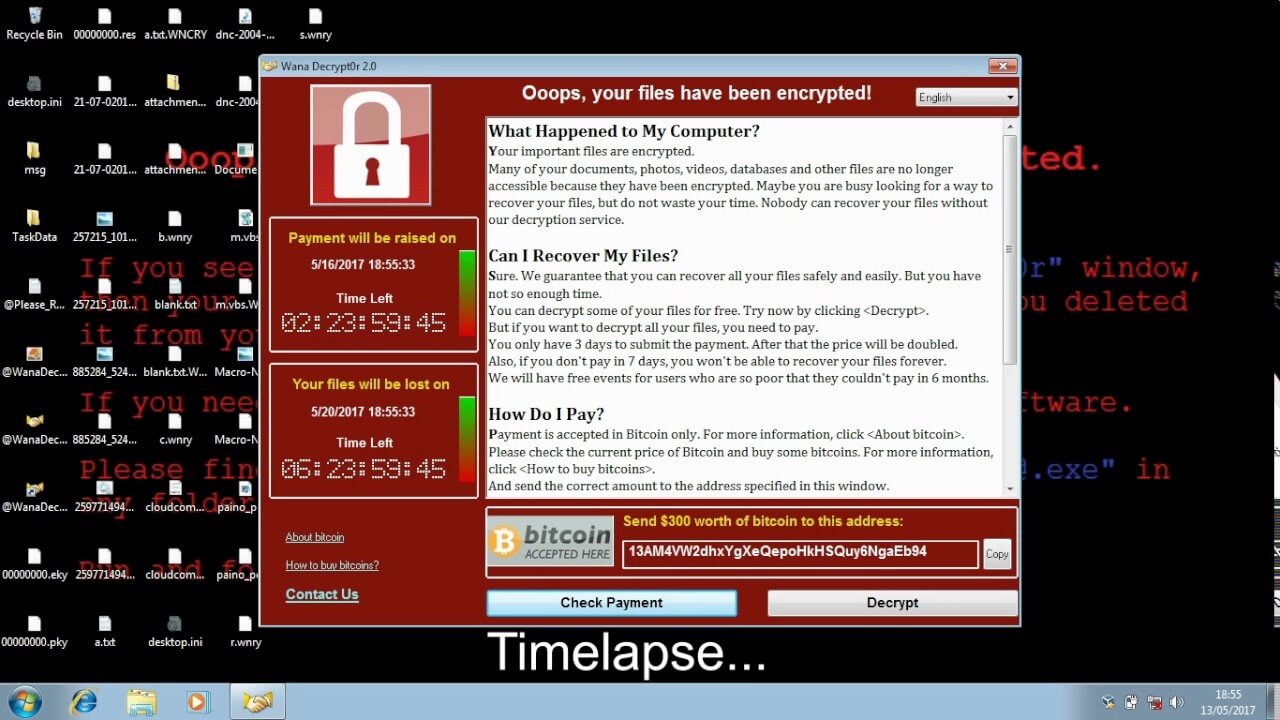
Final step - feign shock & horror, now go home & have the day off.
I have had the fake porn one a couple of times but that was just an email to an account that was in a hacked database. I have never been hit by anything else.
Plesse igmore amd axxept applogies in adbance fir anu typos
One of the guys at work was at Maersk when they got hit by NotPetya, he has some great stories.
I've had a couple of good ones. Had one client get hit, recovered server from backups and all OK...except the finance guy had been archiving email to PSTs (because he always did this) so the emails were no longer on server so that was all lost. They had a proposal to move to 365 on their desk for months which might have helped a smidge.
Had another client pay it, was $1000 or so which was getting off easy.
|
|
|
